Partitioned CRLs
CRL partitioning allows CRLs to be partitioned in several smaller CRLs, instead of one large CRL. This enables you to verify portions of very large CRLs without spending the time to access and validate one large CRL.
CRL partitioning works by assigning each certificate to a random-generated CRL partition number upon issuance. The relying party can map the certificate to the correct partition via the CRL Distribution Point extension, and the CRL can be verified to be the correct CRL from the right partition, by checking its Issuing Distribution Point extension. The functionality is compliant with RFC 5280.
Please verify that your relying parties' software support CRL partitioning before using it. Both the CRL Distribution Point and the Issuing Distribution Point extension must be supported, in the certificate and the CRL respectively. For most use cases, OCSP is a better option.
Configuration
The following tables list configurations required for the CA and Certificate Profile respectively.
CA Configuration
To use partitioned CRLs, the CA must be configured according to the following. For information on all available CA fields, see CA Fields.
|
CA Setting |
Requirements |
|
CRL Specific Data |
|
|
Issuing Distribution Point on CRLs |
Must be enabled. Setting it to critical is strongly recommended for security reasons. This extension is needed so client can check that a CRL belongs to the correct partition. Without this extension (or if non-critical, and not understood by the client), it would be possible to send the wrong CRL to a client, which would then consider all certificates to be not revoked. |
|
Use CRL partitions |
Must be enabled for partitioned CRLs to work. |
|
Number of CRL partitions |
Total number of partitions, and the number of CRLs to generate. This is the highest partition number that will be used in new certificates. Must be at least 1. This value can be increased to scale up with more partitions. Do not decrease this value, unless you are sure there are no certificates in existence with a higher CRL partition. |
|
Number of suspended partitions |
Normally this should be 0, which means there will be no suspended partitions. A suspended partition will not receive new certificates. This value can be temporarily increased to balance the partitions, if the low numbered partitions are larger than the high numbered ones. Since certificates are randomly assigned to a CRL partition, there should be no need to balance the partitions unless the number of partitions has been increased. New certificates will be assigned a partition between (number of suspended partitions + 1) and (number of CRL partitions), inclusive. CRLs are always generated for all partitions, regardless of this setting. |
|
Default CA defined validation data |
|
|
Default CRL Distribution Point |
Certificates must have a CRL Distribution Point (DP) URL which points to the correct partition. The CRL DP URL affects the CRL scope (see RFC 5280, section 5), and must match exactly between the certificate and the CRL. Asterisks "*" are replaced with the partition number (except for partition 0, where the asterisks are removed without replacing). The URL must contain at least one asterisk. If you use the built-in "certdist" URL, all you need to do is to add ¶m=* to the URL. This is done automatically if you click Generate button after enabling the Use CRL partitions option. |
|
Default Freshest CRL Distribution Point |
If using Delta CRLs (also known as the "Freshest CRL" extension), you need to specify an URL with an asterisk for the partition number, in the same way as in the "Default CRL Distribution Point" field. |
Certificate Profile Configuration
The Certificate Profile for issued certificates must be configured according to the following. For information on all available Certificate Profile fields, see Certificate Profile Fields.
|
Certificate Profile Setting |
Requirements |
|
CRL Distribution Points |
Must be enabled |
|
Use CA defined CRL Distribution Point |
Must be enabled |
Certificates that are issued with certificate profiles not configured as above, and any pre-existing certificates prior to activating partitioned CRLs, will have partition number 0.
Example
Let's assume you have the following settings for your CA:
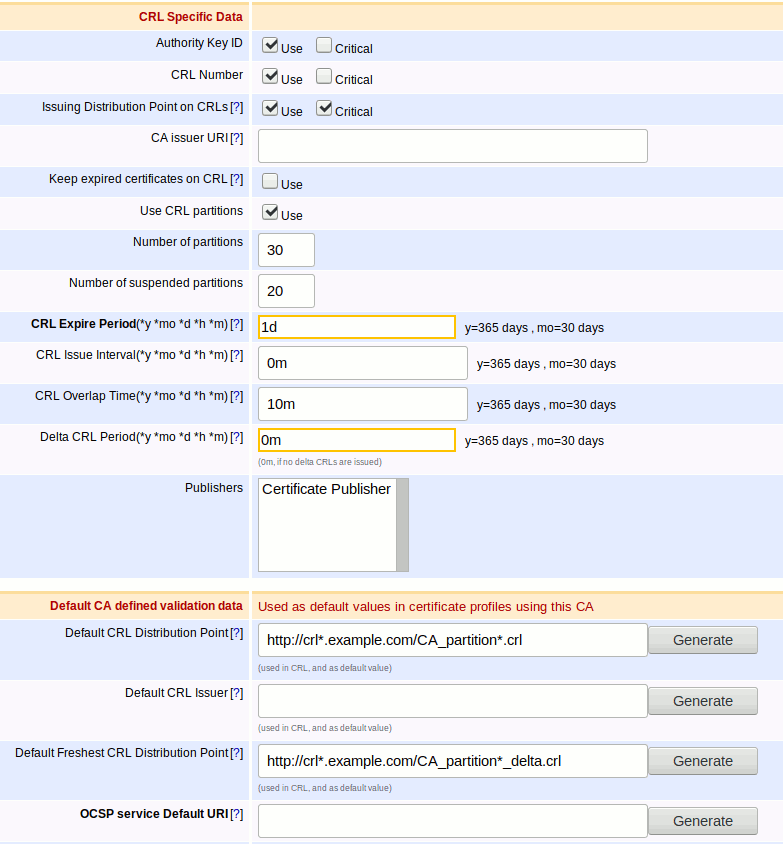
If you then issue a certificate with a certificate profile configured as in the Configuration section, it would be assigned a partition number between 21 and 30, inclusive. The certificate will point to the correct CRL partition using the CRL Distribution Point extension in the certificate. For example, if the certificate was assigned partition 25, then the URL http://crl25.example.com/CA_partition25.crl would be included in the certificate at issuance. Relying parties would then use this URL to check for revocation.
When you revoke the certificate it would go to that CRL partition, and would be included on the CRL the next time it is generated. If the certificate in this example was revoked, then the next time CRLs were generated for the CA, the CRL for partition 25 would contain the serial number of the revoked certificate.
CRL Generation
After a CA has been configured with partitioned CRLs, then requesting creation of a new CRL will generate CRLs for all partitions.
This applies to the CRL Update Worker, CLI, the WebService, the AdminWeb, as well as all operations that indirectly trigger CRL generation, such as CA import or renewal.
CRL Partitioning and Publishing
Certificate publishers and CRL publishers may or may not support partitioned CRLs. Publisher support is shown in the following table:
|
Publisher |
Type |
CRL Partitioning Support |
|
Active Directory Publisher |
Certificate/CRL |
Yes, for certificates. |
|
CertificateSamplerCustomPublisher |
Certificate |
Yes |
|
CertSafePublisher |
Certificate |
Yes |
|
CTCustomPublisher |
Certificate |
Yes |
|
LDAP V3 Publisher |
Certificate/CRL |
Yes, for certificates. |
|
LDAP V3 Search Publisher |
Certificate/CRL |
Yes, for certificates. |
|
Multi Group Publisher |
Certificate/CRL |
Yes (if publishers in groups support partitioned CRLs). |
|
ScpPublisher |
Certificate/CRL |
Yes. |
|
Validation Authority Peer Publisher |
Certificate/CRL |
Yes. |
|
Validation Authority Publisher |
Certificate/CRL |
Yes. |
Fetching CRL Partitions
EJBCA supports fetching CRL partitions by specifying a parameter in the URL. By default, if no parameter is given, it will return CRL partition 0 (which will contain any existing certificates, see Configuration).
The following servlets support retrieving CRL partitions. In the example URLs, the partition number is 123.
|
Servlet name |
Parameter name |
Example URL |
|
certdist |
partition |
http://ejbca.example.com:8080/ejbca/publicweb/webdist/certdist?cmd=crl&issuer=CN%3DExample&partition=123 |
|
search.cgi |
partition |
http://ejbca.example.com:8080/crls/search.cgi?iHash=A0LJKitIFOPr%2BpXooZ7b3EWNyu0&partition=123 |
|
AdminWeb |
partition |
https://ejbca.example.com:8443/ejbca/adminweb/ca/getcrl/getcrl?cmd=crl&issuer=CN=Example&partition=123 Requires client certificate. |
Non-existing partitions are handled the same way as a non-existing CA would be handled. For example, search.cgi will give the HTTP response "204 No Content".
Certificate import
EJBCA supports import of certificates to a CA with partitioned CRLs, as long as the CRL Distribution Point extension is present and exactly matches the value configured in the CA setting Default CRL Distribution Point. The CRL partition number will be extracted from the CRL DP URL.
Certificates that do not meet the requirement above will be imported into partition 0.