Part 6: Prevent Duplicate Certificates
The following covers how to prevent duplicate certificates from being generated by using Custom Certificate Extensions enabled in the Certificate Profile.
Note that commands copy-pasted from this page may need formatting metadata scrubbed and may contain unintended spacing.
Stop Duplicate Certificates from Being Generated
To stop the duplicate certificates from being generated, perform the following steps:
In EJBCA, click System Configuration and select the Custom Certificate Extensions tab.
Specify the following and then click Add:
In Object Identifier (OID), specify 1.3.6.1.4.1.311.21.7.
In Label, specify User Certificate Template Information.
Click Edit on the object added, and specify the following:
Select the Encoding to DEROBJECT.
Enable Dynamic.
Open PowerShell on the CS Host and run the following to obtain the Certificate Template OIDs:
Certutil -catemplates -v | select-string displayname,msPKI-Cert-Template-OIDCopy the portion of the user template OID string following "1.3.6.1.4.1.311.21.8.".
On the Custom Certificate Extensions tab, paste the copied OID string in the Properties table Value field.
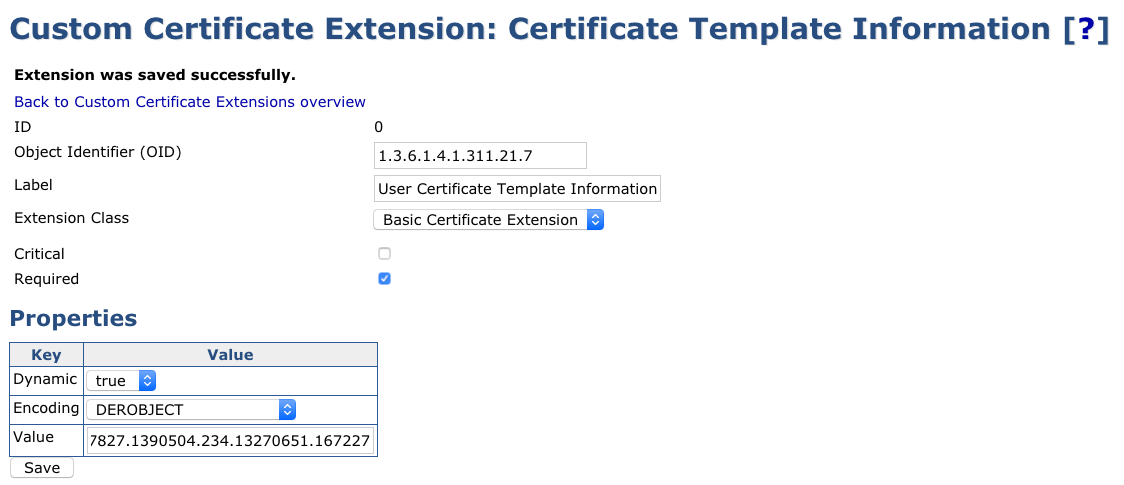
For example, for the following OID:
1.3.6.1.4.1.311.21.8.14060797.2478758.7163562.12957827.1390504.234.13270651.167227paste the following in the Value field:
14060797.2478758.7163562.12957827.1390504.234.13270651.167227Click Save.
Repeat these steps for the Computer Auto Enrollment template, specifying Computer Certificate Template Information as the label, and obtaining the value from the Computer template OID.
Enable Custom Extensions in Certificate Profile
To enable the Custom Extensions in the Certificate Profile, perform the following steps:
Click CA Functions > Certificate Profiles.
Click Clone next to the ENDUSER Certificate Profile and name the new profile User_Certificate_Profile (or select the Certificate Profile already being used).
Click Edit for the User_Certificate_Profile and specify the following:
Key Usage: Digital Signature, Non-repudiation, and Key encipherment (if not already selected).
Extended Key Usage: Client Authentication, Email Protection, and MS Encrypted File System (EFS).
Used Custom Certificate Extensions: User Certificate Template Information.
Available CAs: Issuing CA.
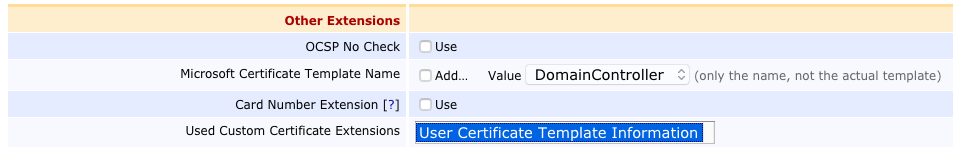
Click Save to save the User Certificate Profile.